Juniper
The CrowdSec Juniper integration allows you to block malicious IPs in your Juniper firewall. This guide will walk you through the steps to integrate CrowdSec blocklists with your Juniper router.
Juniper refers to this feature as Security Dynamic Address feeds, which allow you to import and automatically update IP address lists from external feed servers.
Prerequisites
Before you begin, please ensure your Juniper device supports ingesting blocklists. If you are unsure, please refer to the Juniper documentation or contact Juniper support.
Steps
We will presume you followed the Getting Started guide and have created an account on the CrowdSec Console.
Once you are authenticated, you can proceed to the Blocklist tab located on the top menu bar, from there you can select the Integrations sub menu.
Once the page has loaded, you can click the "Connect" button under the Juniper logo.
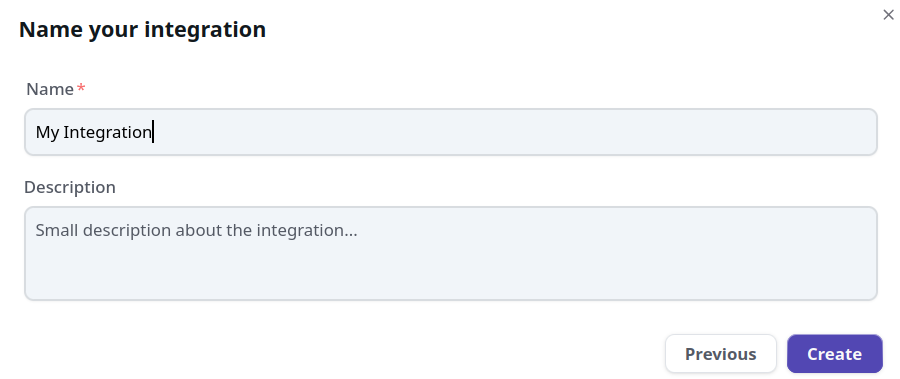
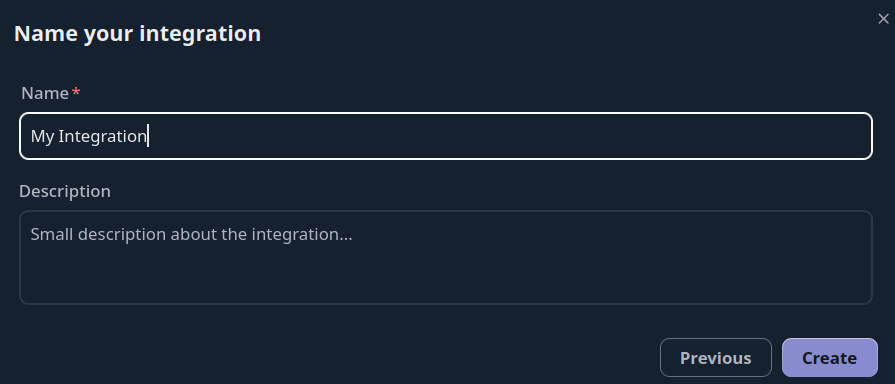
Doing so will prompt you to name this integration, you can name it anything you like, for example "My Integration ". Note the name should be unique per integration that is tied to your account.
Once the integration is generated you will be presented with a credentials screen that will provide you with the necessary information to configure your Juniper Firewall. This information will ONLY be displayed once, so please ensure you copy it down.
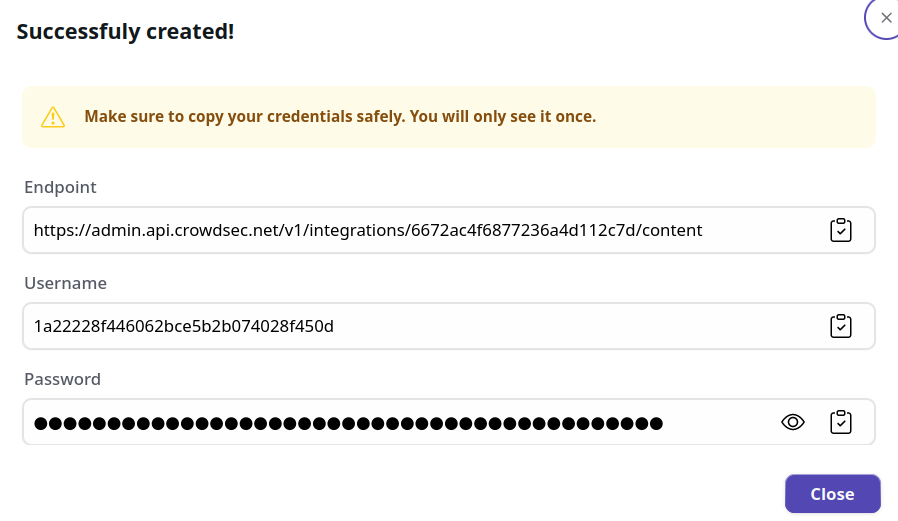
Configuration Example
define the feed server
set security dynamic-address feed-server crowdsec-feed description "CrowdSec Feed"
set security dynamic-address feed-server crowdsec-feed url https://<USERNAME>:<PASSWORD>@admin.api.crowdsec.net
define the threat feed and the update interval
set security dynamic-address feed-server crowdsec-feed feed-name crowdsec-feed description "CrowdSec Feed"
set security dynamic-address feed-server crowdsec-feed feed-name crowdsec-feed path /v1/integrations/<integration_id>/content
set security dynamic-address feed-server crowdsec-feed feed-name crowdsec-feed update-interval 1440 hold-interval 43200
Define AddressName-to-ThreatFeed mapping
set security dynamic-address address-name crowdsec-feed address-name crowdsec-feed feed-name crowdsec-feed
Review and commit the configuration
show security dynamic-address
The output should look like this:
feed-server crowdsec-feed {
description "CrowdSec Feed";
url https://<USERNAME>:<PASSWORD>@admin.api.crowdsec.net;
feed-name crowdsec-feed {
description CrowdSec Feed;
path /v1/integrations/<integration_id>/content;
update-interval 120;
hold-interval 43200;
}
}
address-name crowdsec-feed {
profile {
feed-name crowdsec-feed;
}
}
Format example
The CrowdSec blocklist will be in plain text format, with one IP address per line. Here is an example of how the blocklist will look:
192.168.38.187
192.168.38.186
Manage integration size limits with pagination
If you want to learn how to manage integration size limits with pagination, please refer to the Managing integrations size limits with pagination section.
Contribute to this documentation
Since CrowdSec is a community-driven project, we welcome contributions to this documentation. If you have any instructions or tips that you would like to share with the community, please feel free to open a pull request on our GitHub repository
Next Steps
Now that you have integrated CrowdSec integration with your Juniper firewall, you can proceed to the Blocklist Catalog to find what blocklists you can subscribe too.

